We may reveal issues of our network that exhibit themselves in other networks, we may be prepared on the threats to come. So let's move the information sharing to the next level to improve overall network situation awareness and render our networks more resilient in the long term.
At present, the protection of networks, services and users against cyber attacks is mostly assured independently, that is, by each entity (ISP, company, data centre, ...) itself. These entities often detect security events (indicators of compromise such as vulnerability exploit, brute force attack,...) affecting their infrastructure and adopt countermeasures based on the results and their security policy. Network operators, service providers and security teams share only a limited amount of information about the detected events. Thus, such data are not fully exploited for visibility and protection of the infrastructure as a whole. Therefore CESNET and Masaryk University have decided to build and operate a system for sharing and analysis of security events in Czech cyberspace, called SABU.
In general, the benefits of joining SABU community are multifold but primarily partners get access to the events shared by others. We realize that shared events are too low level but we do not want to rob partners of full control over data processing. If you are interested in higher level you opt for customized email reports that prioritize and aggregate events according to a dedicated profile. A popular use case is to observe if my IP addresses are being reported by others, in other words, is my network source of problems that are detected by others? A proof-of-concept deployment at CESNET, Masaryk University and other partners' organizations has already proved useful by the positive feedback from the partners. For example, several SABU partners already utilize reported information to correlate events reported by other sources (e.g. by honeypots) to discover compromised machines faster and more precisely. Besides this particular use case, there are plenty more to come, such as advanced reputation database, attack mitigation and prediction of upcoming attacks.
Although the project broad deployment and complete functionality will be available in 2 years, it is possible to start joining it by automatically sharing selected security events into Warden system which is a part of SABU system. In case you already have deployed Flowmon ADS joining SABU is as simple as uploading the Warden plugin into Flowmon and registering your Flowmon ADS into the sharing system. The Flowmon ADS to Warden connector acts as any other reporting script that you may already use, for example, to send reports on selected events by email, thus it is easy to customize what events are being reported. When SABU will become fully operational, Flowmon ADS will access SABU to recognize IP addresses of bad reputation. As a result Flowmon ADS will be able to not only highlight suspicious communication but also to increase monitoring details and lower detection thresholds in case of these IP addresses.
Figure 1: The principle of SABU system
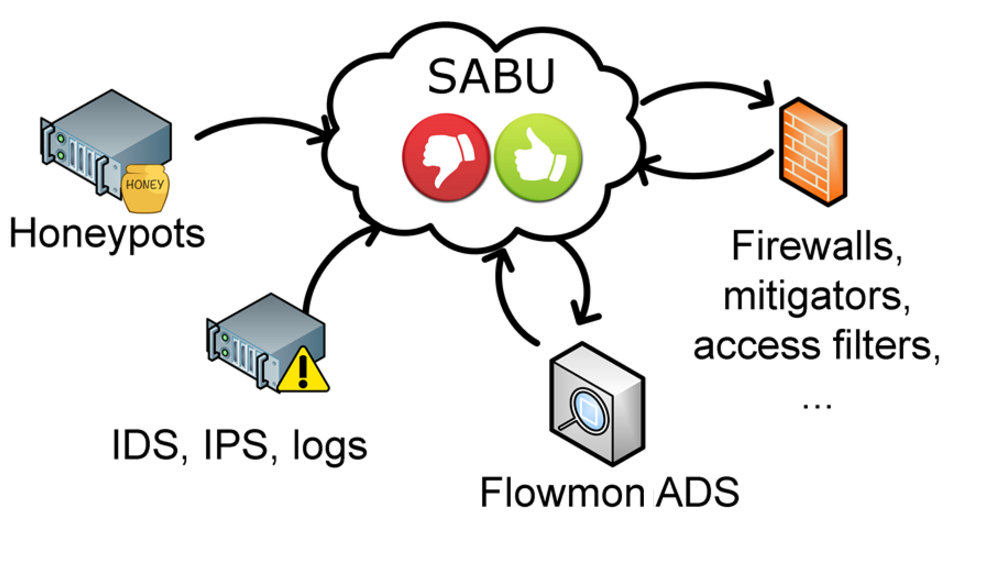
We have been testing the Warden connector in our Flowmon ADS deployments at CESNET and Masaryk University for more than three months. The connectors report approximately 500 events per day in summary but this highly depends on the setup of the reporting. The reporting shows no effect on the Flowmon performance itself. As of today we successfully collect events from a wide range of reporting systems ranging from honeypots, server logs and newly also from flow behavioral analysis tools such as Flowmon ADS. Despite the so far limited deployment we are already able to observe correlations among events and, indeed, the SABU now acts like an inter-organization SIEM. You may be interested in our technical reports describing events correlations [1].
To conclude, the sharing of information on network security events is becoming a reality as the number of sources that already share similar information ranges from various blacklist maintainers, antivirus vendors to dedicated teams such as Team Cymru, Shadowserver and further are emerging. Flowmon Networks is commercial partner of SABU project. Flowmon ADS implements Warden client to deliver selected events to central Warden server. This feature is avalable to all Flowmon customers with Flowmon ADS version Business or higher versions or Flowmon ADS ISP all versions. According to our experience Flowmon ADS is a great source of network intelligence and we hope that SABU will interest Flowmon ADS users to join the community, for more information please visit SABU web page [2].
[1] V. Bartos: Analysis of alerts reported to Warden, online: https://www.cesnet.cz/wp-content/uploads/2016/03/alert-analysis.pdf
[2] SABU web page, online: https://sabu.cesnet.cz/en/about_project