How Indicators of Compromise Are Made?
Did you ever wonder how indicators of compromise are created? In addition to cyber security professionals who’s daily job is to reverse engineer malware and publish indicators of compromise, there is a large security community that protects various environments, detects and blocks malicious activities literary every second. This effort produces large volume of logs that contain very interesting information, particularly indicators of compromise in the form of IP addresses of attackers. To unlock the value hidden in the logs, extraction of indicators of compromise and sharing with the community is required.
Flowmon ADS & MISP Integration
This is exactly what we did in the context of our Network Detection & Response capabilities. Flowmon ADS provides various detection techniques based on machine learning, adaptive baselining, heuristics or behavior pattern to detect broad set of adversary activities at scale and without signatures. Coverage of unknown attacks is essential to produce valuable indicators of compromise.
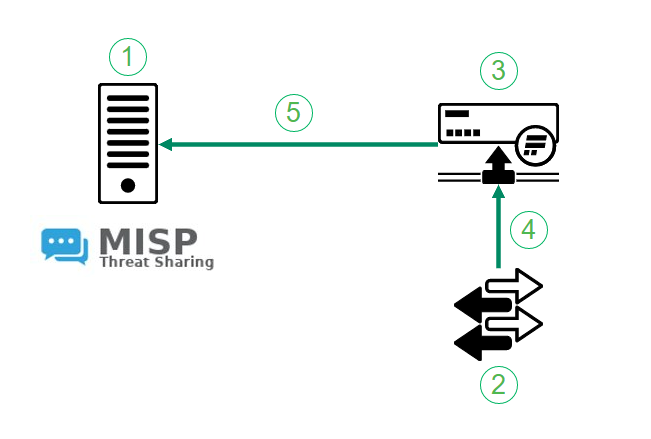
The integration of Flowmon ADS and MISP to feed events into MISP as indicators of compromise. (1) Server running a customer’s instance of MISP platform. (2) Network element, e.g. core switch. (3) Flowmon appliance running Flowmon ADS for advanced threat detection. (4) Port mirroring to Flowmon appliance. (5) Implementation of MISP API to export indicators of compromise extracted from Flowmon events.
The concept of custom scripts in Flowmon ADS is the basis of an integration script that converts an event detected by Flowmon ADS into a standard MISP event with attached indicators of compromise as attributes. Events that are converted to indicators of compromise and exported to MISP are controlled by perspectives and private IP addresses are filtered automatically. Additional IP addresses can be filtered as required. The complete installation manual is part of the integration script, which is publicly available at https://github.com/progress/ADS-MISP.
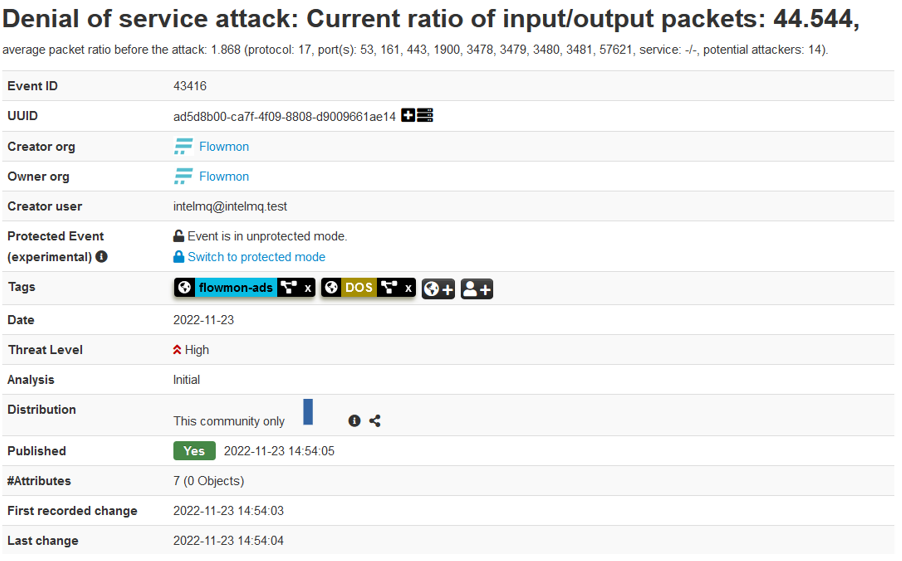
See above event created in the MISP platform automatically from malicious activity detected and reported by Flowmon ADS.
This is our pay back to the cyber security community. Any Flowmon appliance can be part of joint global effort to make the internet more secure place. All Flowmon customers can leverage the integration free of charge together with Flowmon ADS 12.0 or newer.
This work is part of the Cyber security competence for research and innovation (CONCORDIA) project under the grant agreement no. 830297. 
