Mitigation tiering is a mechanism that DDoS Defender uses to respond to attacks of varying magnitude by employing mitigation that is proportional to the size of the attack. It is a faster and more cost-effective way to protect a large number of customers in a world where attacks are hard to predict.
Users can utilize multiple mitigation techniques to better protect their network infrastructure and customers. Mitigation tiering is based on a defined threshold that is compared with the volume of redirected traffic and is then able to use additional BGP communities when the threshold is exceeded.
Additional features:
- IPv6 Flowspec filters and actions supported for BGP
- New email alert macro for overall traffic which shows the volume of current total traffic and normal traffic to provide context about the magnitude of DDoS attacks
- Script-based integrations are improved thanks to signature updates, allowing for mitigation fine-tuning
- Performance has been improved thanks to optimization in the number of channels per profile
Let’s take a look at the following example to see how it works in practice.
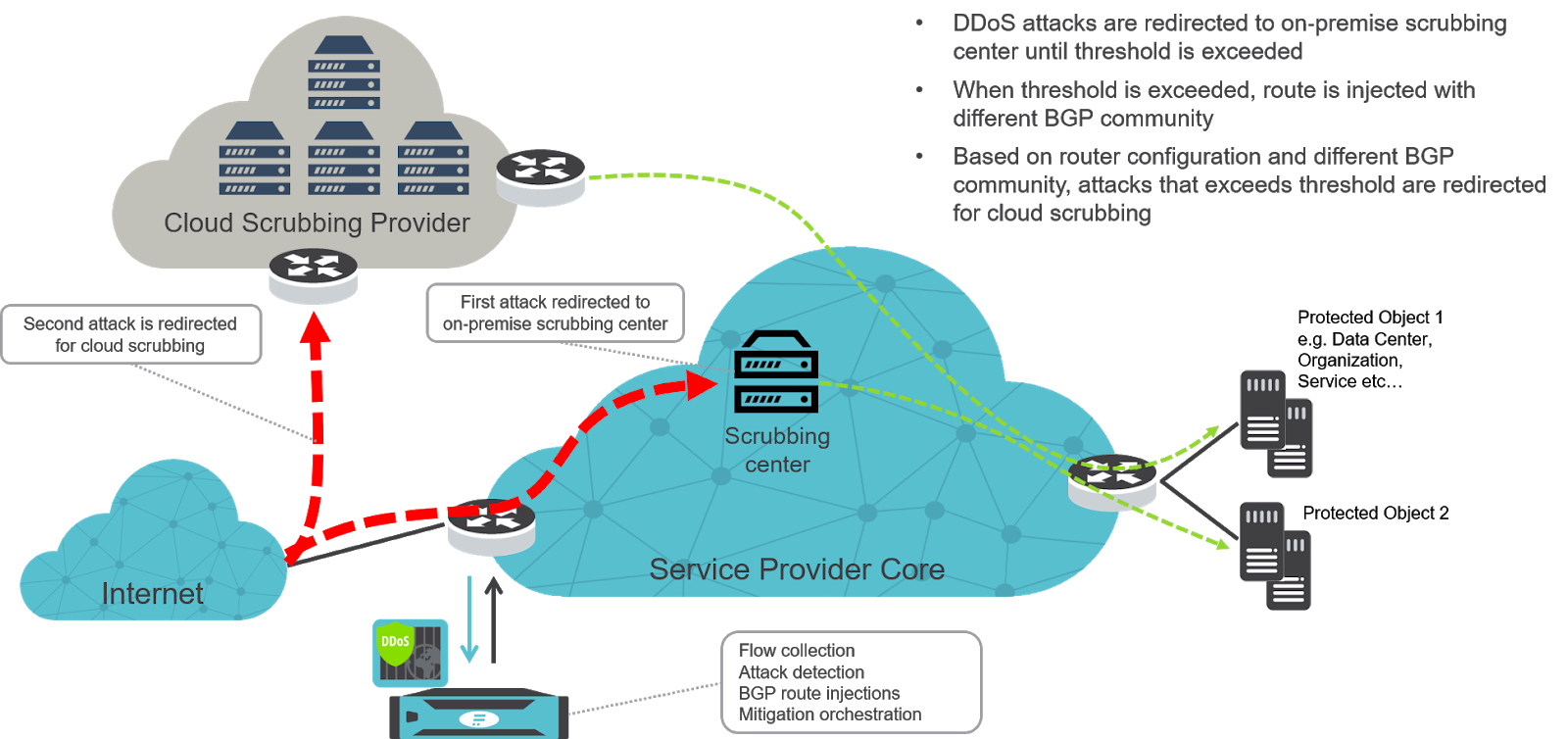
An internet service provider offers a DDoS protection service to its customers. They have an out-of-path DDoS protection solution based on Flowmon DDoS Defender and use a scrubbing center to clean the attack traffic, which is redirected to it when Flowmon detects an attack. However, the scrubbing center has limited capacity and the ISP is therefore limited by the size of attacks that can be redirected to the scrubbing center.
This is the reason why ISPs have a ‘backup plan’, which can be another mitigation technique, device or service. In this case, it is the service of a cloud scrubbing provider. Using mitigation tiering, the ISP can automatically redirect attacks which exceed the on-premise scrubbing center capacity. All they need to do is configure the threshold based on the capacity of the scrubbing center. When the next incoming DDoS attack is larger than the threshold, an additional BGP community is used to mark the route (victim’s subnet) and based on the router configuration, the attack is redirected to the cloud scrubbing center. There, the traffic is cleared, so that only legitimate traffic is sent to the ISP’s customers.
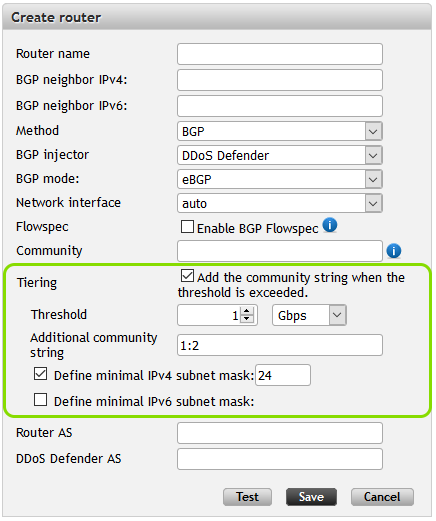
Tiering can be enabled in router configuration and two thresholds can be used - the first for the router and second for the protected segment. Both are evaluated independently. This provides granularity for different BGP communities and thus allows the use of different mitigation techniques. It is also possible to define a minimal subnet mask, e.g. when the route needs to be propagated to the Internet. The configuration can be changed when manual mitigation is used in cases where the user reconsiders using the additional BGP communities or wants to make changes in the configuration before the mitigation is started.
Mitigation tiering in Flowmon DDoS Defender 4.5 ensures a more robust and reliable attack response. It will remain an important asset in the upcoming DDoS Defender 5, which will receive additional improvements such as faster attack detection thanks to stream data processing. Its increased detection accuracy will make even more effective use of mitigation tiering, as will the improved segment management and baseline analysis.
Keep your eye out for the news.
If you are interested in additional information, do not hesitate to contact us.