Faced with the latest development in IT infrastructures, perhaps made even worse by recent global events, security admins may find that their existing tools give them visibility that is at best nebulous - and not just because of the cloud. Even though endpoint protection consumes a substantial part of the security budget, breaches still happen and sensitive data gets stolen. Moreover, endpoint visibility is not always complete. How many servers are actually covered? Or industrial or medical equipment? And now that many staff members work remotely and service providers receive greater access to company networks, can you really be sure users can be trusted and will keep their devices secure?
Of course, security operations routinely use SIEMs to deal with such issues. Capable though they are, every SIEM is only as powerful as its data source. Without reliable feeds and sufficient coverage, the SIEM is blind. Attackers can also tamper with logs to mask their movements and in some cases, logging may even be turned off to save up on performance. This means that there is a risk that threats are being missed among floods of false positives or are slipping through visibility gaps.
There is strength in diversity
This line of thought has been picked up by Gartner, who developed it into a concept called the SOC Visibility Triad consisting of three complementary pillars. Two of the pillars are SIEM and Endpoint Detection and Response (EDR). The third is called Network Detection and Response, or NDR (formerly called Network Traffic Analysis - NTA). NDR adds the network perspective to the model and thus completes the SOC Visibility Triad.
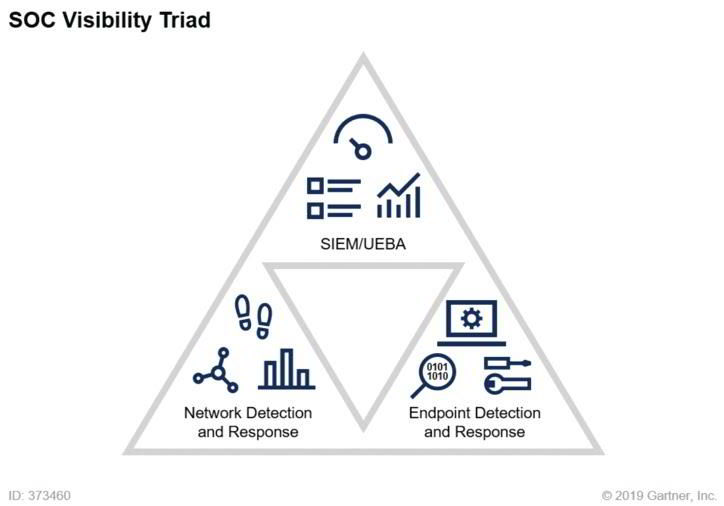
Source: Applying Network-Centric Approaches for Threat Detection and Response, 2019, Gartner ID G00373460
The idea behind the Triad is strength in diversity - the capabilities of each solution make up for the weaknesses of the other two. EDR is the only window into endpoints, SIEMs can process the wealth and depth of logs (and even use network data as a source), and NDR offers the holistic network perspective. So, although NDR cannot see into endpoints and does not provide the same depth as logs, in some cases, it may even be the only layer of defense, since not every endpoint allows installing an agent and SIEMs may not always see everywhere.
To better understand how NDR fits the Triad, consider the following example. While on a business trip, the laptop of a company employee was infected by ransomware. Upon returning and connecting to the company network, the ransomware scans it for exploitable devices. Eventually, the attacker discovers a vulnerability and manages to covertly obtain access credentials. With those in hand, they find their way to sensitive private data, which they encrypt, split into chunks, and begin exfiltrating as innocent ICMP communication.
Now, EDR and SIEM should certainly be able to detect such activity at some point. But still, news of ransomware attacks appear regularly in the news.
Another layer of protection
It is in cases such as this that the network-centric approach comes to its own. At every stage of the attack, the adversary leaves footprints in network traffic that are extremely difficult to cover, which enables NDR to add a consistent level of reliability to the Triad. And while it is by no means a replacement for EDR or SIEM, it is an essential component in the kind of layered security that is required to combat modern threats.
For more about combating ransomware with the network-centric approach, watch our webinar.
Early adopters of the Triad have so far been large enterprises, partly because they are lucrative targets and their need for protection is greater, and partly because they could afford to do so. But advancements in network monitoring technology (e.g. thanks to L7-enriched flow data, which now provides visibility that is competitive to packet capture), make NDR solutions lightweight enough to be available also to mid-sized businesses or organizations with stricter budgets, such as governments and healthcare institutions. Like the car or telephone a century ago, NDR (and thus the whole SOC Visibility Triad) is becoming a fact of life for a much broader audience.
It may seem that adding another tool would only increase the mess, but the opposite is true. Insight from NDR tools speeds up triage and investigation, and improves the productivity of the whole security by supporting automation and enabling prompt response. Without an NDR tool, you will have a hard time validating Indicators of Compromise as well. And in light of the ever-increasing adoption of cloud platforms, NDR covers blind spots in visibility in spite of the fact that the digital environment is sprawling beyond the confines of company premises.
Minimize the chances of a successful attack
When Anton Chuvakin of Gartner first mentioned the SOC Nuclear Triad back in 2015, he drew inspiration from a doomsday scenario from the Cold War. While the Nuclear Triad thankfully never got to be tested, the SOC Visibility Triad has withstood multiple tests and has more than lived up to its original purpose - to significantly reduce the likelihood that an attacker will be able to achieve their goal.
Related Articles:
What is Network Detection and Response (NDR)?